When people think about cybersecurity, they often imagine firewalls, tools, and complex systems. But one of the most underrated security skills is not technical at all. It is structure. Structure is what keeps things from falling apart when humans get tired, rushed, or distracted. And since humans are always part of the system, structure becomes a form of protection. In security and GRC, structure shows up as policies, procedures, playbooks, and clear roles. Not because people don’t care but because caring alone is not enough. When there is no structure, decisions are made on the fly. And decisions made under pressure are where most security incidents begin. Structure removes guesswork. It tells people: Without structure, security relies on memory, good intentions, and “common sense.” And those fail when urgency, fear, or convenience enters the picture. Think about incident response. When something goes wrong, the goal is not to panic it is to follow a plan. That plan exists so people don’t have to think under stress. They just act. That is structure doing its job. Structure is also what turns awareness into action. Training tells people what could happen. Structure tells them what to do when it does. This is why GRC values documentation, reviews, and consistency. It is not paperwork for the sake of paperwork. It is a safety net. A way to protect people from their own limits. Strong security systems don’t expect humans to be perfect.They expect humans to be human and they build structure around that reality. Because in cybersecurity, structure doesn’t slow you down.It keeps you safe when it matters most. And that is why structure is not boring.It’s a skill.A security skill.
Why I Chose GRC in Cybersecurity
When I first decided to move into cybersecurity, I didn’t know how wide the field really was. To me, cybersecurity was just… cybersecurity. I didn’t yet understand that it had many different roles, paths, and specialisations. That clarity only started to come after training. During my cybersecurity training, I was exposed to different areas, but I still hadn’t made a decision. I was learning, observing, and trying to understand where I fit. The Internship That Helped Me Be Honest With Myself I got an opportunity to intern remotely at a cybersecurity company for one month. During that time, we were taught more about penetration testing and report writing. And this is where something important happened. I was bored. Not because the work wasn’t important but because it didn’t spark anything in me. I paid attention to how I felt and chose to be honest with myself. I realised that this side of cybersecurity didn’t excite me, and pretending otherwise wouldn’t help my journey. That honesty mattered. Discovering Cyber Threat Intelligence Later on, I took a course in Cisco Cyber Threat Intelligence. This experience felt completely different. I loved it. It sparked my curiosity. I enjoyed understanding threats, patterns, behaviours, and why attacks happen not just how they happen. For the first time, I felt engaged instead of forcing interest. That curiosity pushed me further. The Moment I Found GRC I started watching more videos on YouTube, especially content related to risk management. That was when I came across GRC; Governance, Risk, and Compliance. Something clicked. I found myself drawn to this side of cybersecurity and couldn’t immediately explain why. So I asked myself a simple question: Why am I drawn to GRC? Connecting the Dots With My Work Experience Out of curiosity, I typed that exact question into ChatGPT. I explained my background, that I had been a flight attendant for over a decade. The response stopped me in my tracks. I was told that I was likely drawn to GRC because compliance, regulations, procedures, and safety rules had been part of my life for years. And that was true. As a flight attendant, compliance wasn’t optional. Regulations had to be followed. Procedures existed for a reason. Safety depended on structure, accountability, and consistency. I wasn’t starting something new.I was recognising something familiar. Why GRC Makes Sense for Me GRC focuses on: It’s about understanding what could go wrong, how to reduce the impact, and how to respond when things don’t go as planned. That mindset felt natural to me. On A Final note…. Choosing GRC wasn’t about chasing a title or forcing a role.It was about paying attention to my interests, my curiosity, and my past work experience. Cybersecurity is a big field.Finding your place in it starts with honesty. For me, GRC didn’t feel foreign.It felt like home just in a different industry.
Why Convenience Is The Enemy Of Security
In the beginning, convenience felt harmless. When I first started using social media, I didn’t think much about passwords. I wasn’t careless I was being practical. Using the same password for all my accounts made life easier. One password to remember. No stress. No confusion. It felt efficient. And honestly, I thought, “At least I won’t forget it.” What I didn’t understand then was that convenience quietly trades comfort for risk. When Convenience Feels Smart….Until It Isn’t Using one password everywhere worked… until it didn’t. When my Google account was taken over, the process of getting it back was long and exhausting. Emails. Verifications. Waiting. Proving ownership again and again. It took time, patience, and persistence before I finally recovered it. That experience alone was sobering. But when my Facebook page was taken over, I made a different decision. I didn’t fight for it the same way. I simply started again and built a new one from scratch. Not because it didn’t matter but because the cost of recovery felt heavier than starting over. Both experiences taught me something I had ignored before. Convenience Creates Single Points of Failure The problem with convenience is not that it is wrong it is that it concentrates risk. One password across multiple platforms means one mistake opens many doors. Once that password is exposed, everything connected to it becomes vulnerable. I didn’t fully understand this until I lived through the recovery process. It was during that time resetting access, securing accounts, rebuilding that the importance of passwords finally became clear to me. Security Is Designed to Be Inconvenient for a Reason Security slows you down on purpose. Multiple passwords.Verification steps.Authentication codes. All of these things feel inconvenient because they interrupt ease. But that interruption is intentional. It exists to protect you during moments when convenience would otherwise cost you everything. Attackers depend on ease.Security depends on friction. And most people are not patient, we are always in a hurry. What Changed for Me After those experiences, I stopped prioritising convenience over protection. I began to see passwords not as obstacles, but as boundaries. I understood that the slight discomfort of managing them properly was nothing compared to the stress of losing access and control over my digital life. Convenience had taught me comfort.Security taught me responsibility. Final Thought Convenience feels good in the moment.Security protects you in the long run. Most security failures don’t happen because people are reckless they happen because people choose what feels easiest. And sometimes, the easiest choice is the most expensive one. Want more like this?I write about human-centred cybersecurity, risk, and career transitions.
Why Attackers Don’t Hack Systems,They Hack People Instead.
Before attackers go after systems, networks, or software, they go after something far more powerful: the human mind. That’s where the real game is played. As human beings, we are wired in very specific ways. We trust. We help. We respond quickly to urgency. We don’t want to miss opportunities. We don’t want to get into trouble. These traits help society functionbut they also make us vulnerable. Attackers understand this better than most people realize. They don’t need to break technology if they can influence behaviour.And influencing behaviour starts in the mind. The Mind Is the First Attack Surface Cyberattacks don’t begin with code.They begin with emotions. Fear.Pressure.Excitement.Authority.Opportunity. Once an attacker triggers any of these, critical thinking often slows down. Logic steps aside, and reaction takes over. At that point, the hardest part of the attack is already done. Systems Are Built to Resist ,Humans Are Built to Trust Modern systems are designed with layers of protection: passwords, firewalls, encryption, and access controls. Breaking through them directly takes time, skill, and effort. Humans, on the other hand, are not built to resist they are built to connect. We assume good intent.We respond when something sounds important.We act quickly when consequences are mentioned. Attackers exploit this difference. So instead of fighting the system, they go around it by targeting the person using it. People Are the Easiest Entry Point An attacker doesn’t need advanced tools if they can simply: Once a human opens the door, the system behaves exactly as designed. No hacking required. Just manipulation. Social Engineering Is About Psychology, Not Technology Social engineering works because it speaks to emotions, not logic. Messages are crafted to sound: When emotions rise, verification drops. This is why so many successful attacks involve phishing emails, fake support calls, job offers, or warnings about account problems. The technology isn’t failing it is the human moment that is being exploited. Why Awareness Is the Real Defense Security tools matter, but they can’t replace awareness. Cybersecurity depends on people knowing when to pause, when to question urgency, and when to verify through another channel. This is why cybersecurity is not just a technical field.It’s a human one. Final Thought If attackers can control your emotions,they can control your actions. And once they control your actions,they don’t need to hack any system at all. The strongest defense isn’t fear it’s awareness, patience, and understanding how the mind is used in attacks. Remember to ‘Never Trust, Always Verify’
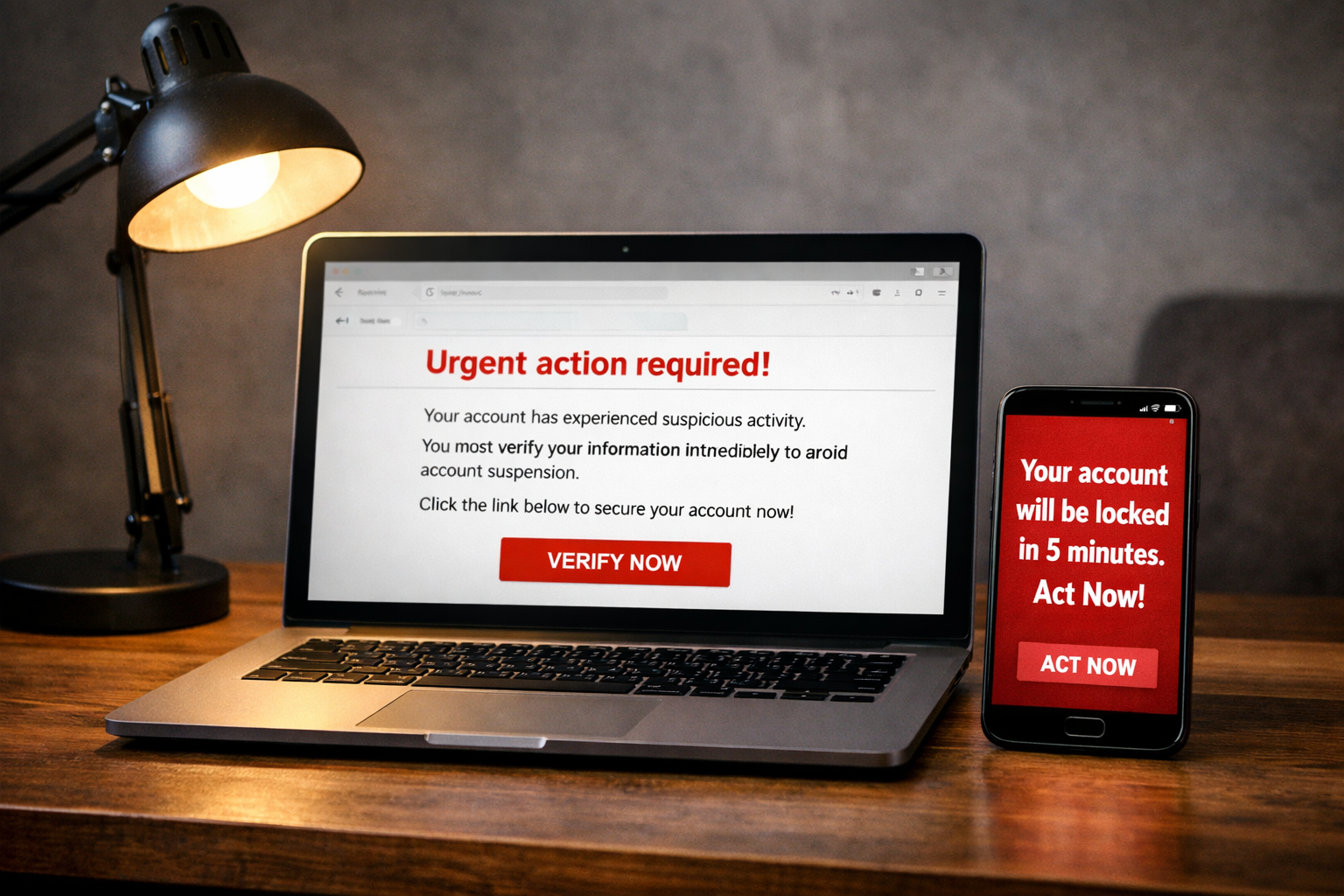
The Most Dangerous Word In Cybersecurity Is ‘Urgent’
In cybersecurity, many attacks don’t start with hacking tools or technical tricks. They start with one word: Urgent. That word has caused more people to lose accounts, money, and data than most viruses or malware. Why? Because the moment something feels urgent, people stop thinking clearly. Attackers know this very well. Why Attackers Use the Word “Urgent” When something feels urgent, fear kicks in. You feel pressure to act fast so you don’t lose something important. Once fear takes over, logic goes quiet. That’s why attackers use messages like: The goal is simple:make you panic so you act without thinking. Urgency Makes People Skip Checks When people feel rushed, they don’t verify.They don’t double-check links.They don’t ask questions.They don’t slow down. They click. They respond. They approve access. And once that happens, the damage is already done. Most cyber incidents happen not because someone is careless, but because they felt pressured to act quickly. Good Security Slows You Down Strong security systems are designed to slow people down on purpose. That’s why important actions need: These steps are not there to annoy you.They are there to protect you when emotions are high. Urgent Does Not Always Mean Real Not everything urgent is true.Real companies give you time to verify.Real problems can be checked through official channels. Fake urgency falls apart when you pause and question it. The Real Skill Is Control Cybersecurity is not about acting fast.It is about acting wisely. When you slow down, you take back control.And when you take back control, most attacks fail. Final Thought If a message tells you to act immediately, pause.Take a breath.Verify first….. Never Trust, always verify! Want more like this?I write about human-centred cybersecurity, risk, and career transitions.
Why Slowing Down Is A Security Skill
In cybersecurity, speed is often praised. Fast detection. Fast response. Fast recovery. But there’s a quieter skill that prevents more incidents than most tools ever will: Slowing down. Many security incidents don’t happen because systems fail. They happen because humans move too fast. A rushed click. A hurried response. An emotional reaction to pressure. Attackers understand this deeply and they exploit it. They don’t need you to think.They need you to react. Urgency Is Designed to Create Fear Urgency is not accidental. It is deliberate. When urgency enters a message, it creates fear. And once fear takes over, rational thinking steps aside. At that point, the attacker doesn’t need access to your system they already have access to your mind. This is how control is gained. Reflect for a moment on situations in your life where it felt like if you didn’t act immediately, something terrible would happen. A missed opportunity. A lost account. A looming consequence. Now ask yourself:How many times did you fail to meet that urgency… and heaven did not fall? That realisation alone is powerful. Social Engineering Is a Mind Game Social engineering does not rely on technology. It relies on psychology. It plays on: Once emotion takes the lead, logic struggles to catch up. That’s why slowing down matters. Slowing Down Restores Control Slowing down breaks the spell. It gives you space to ask: Most malicious requests collapse under simple scrutiny. From a security perspective, slowing down reduces risk. It increases verification, limits impulsive decisions, and prevents attackers from steering your actions. Patience Is a Security Virtue In cybersecurity, patience is not weakness it is strength. Mature security systems are designed to slow people down on purpose: confirmation steps, approvals, reviews, and delays. These controls exist because humans are emotional, and emotions can be exploited. Slowing down protects not just systems, but people. Final Thought Social engineering is a mind game.Security is knowing when not to play. Slow down.Question urgency.Trust verification over fear. And sometimes you need toslow down and smell the cookie. Because control begins the moment you pause. Want more like this?I write about human-centred cybersecurity, risk, and career transitions.
Personal Digital Hygiene Tips for the Holiday Season
The holiday season is a time for joy, travel, reconnection, and celebration. It’s also a season when many of let our guard down online and offline. Unfortunately, attackers know this too. When we are distracted, excited, or eager to share good moments, our digital hygiene often slips. That is why being intentional during this season matters more than ever. Think of digital hygiene the same way you think of personal hygiene:small, consistent habits that quietly protect you. 1. Be Mindful of What You Share Especially During Travel To my fellow African brothers and sisters travelling home to celebrate:resist the urge to show off. The “I have arrived” mentality of posting locations, arrivals, gifts, or lifestyle updates in real time can expose you and your loved ones to unnecessary risk. Protect yourself and your family by: Privacy is protection. Not everything needs an audience. 2. Keep Certain Things Private for Your Own Safety Not everyone watching your posts has good intentions.Some people are observing quietly, connecting dots, and gathering context. What feels like harmless celebration can become useful information to someone with the wrong motives. Digital hygiene means knowing that: 3. Be Extra Careful with Holiday Messages and “Opportunities” During the festive season, messages increase giveaways, offers, collaborations, job promises, and quick favors. Slow down before responding. You don’t owe strangers access to your time or your trust. 4. Young Ladies: Be Intentional About Online Relationships This part matters. Please don’t fall for “he said he lives abroad” as proof of legitimacy.Photos can be edited. Stories can be curated. Lifestyles can be staged. It is incredibly easy to make life look a certain way online. And the truth is simple:you don’t need someone abroad to validate your worth or your future. If you’re earning a decent salary, building your life, and growing you can travel abroad by yourself. You don’t need illusions sold through messages and filtered photos. Digital hygiene also means emotional hygiene. 5. Use Strong Passwords and Enable 2FA Avoid passwords linked to anything visible on your social media names, dates, locations, hobbies. Make sure Two-Factor Authentication (2FA) is turned on for: That extra step protects you when emotions or distractions creep in. 6. Be Careful with Direct Messages Scammers love the holidays because people are more open and less guarded. If a message feels: Pause and Verify. 7. Awareness Is the Real Gift Digital hygiene is not about fear.It is about intentional living online and offline. Understanding that: …is one of the strongest forms of protection you can give yourself and your family. Final Thought Enjoy the holidays.Celebrate fully.Reconnect with loved ones. Just remember:what you keep private today can protect you tomorrow. Security starts with awareness and awareness is always in season. Merry Christmas!
Why 2FA and Multi-Factor Authentication Matter More Than You Think
For a long time, I believed a strong password was enough. If it was long, unique, and “hard to guess,” I felt protected. What I didn’t understand back then is this: Passwords don’t fail people do.And attackers know that. After experiencing social engineering firsthand, I learned a painful but important lesson: once an attacker convinces you to hand over access, your password becomes irrelevant. That’s where Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) step in not as an inconvenience, but as protection for very human moments. What 2FA and MFA Really Are….. Two-Factor Authentication (2FA) means proving your identity in two different ways.Multi-Factor Authentication (MFA) simply adds even more layers. These layers usually fall into three categories: When more than one of these is required, stealing just one is no longer enough. Why Passwords Alone Are Not Enough Social engineering doesn’t crack passwords it bypasses them. Attackers rely on: Once they convince you to share a code or approve access, the system believes the request is legitimate. I have lived this. That is why 2FA and MFA exist, not because users are careless, but because humans are human. We get distracted. We get hopeful. We trust. We move fast. Security has to account for that reality. 2FA as a Human Safety Net One of the most important apps on my phone today is my authenticator app.Without it, even I cannot log into some of my own accounts. And that’s a good thing. Till today, I still receive authentication prompts, emails or messages asking me to verify my identity because someone, somewhere, is trying to log in. Those alerts are reminders that threats don’t stop just because time has passed. 2FA acts like a second voice asking:“Are you sure this is really you?” Even if an attacker gets your password: That pause, that interruption is often enough to stop an attack in its tracks. Security Is Everyone’s Responsibility Security isn’t just for tech professionals or cybersecurity teams.It is a shared responsibility. Being secure doesn’t mean being paranoid but it does mean being intentional.It means slowing down.Verifying before trusting.And understanding that convenience should never come at the cost of control. Don’t be too trusting.Trust, but always verify. In my next post, I’ll go deeper into social engineering, using my personal experiences to show how attackers think and how easily trust can be manipulated when we’re not paying attention. Because understanding the human side of security is where real protection begins.
The Psychology Of Trust: How Attackers Exploit Human Nature
Before I started learning cybersecurity, I believed attacks were loud systems breaking systems. What I didn’t understand then is that many cyberattacks don’t begin with technology at all. They begin with trust. Trust is what allows us to believe the best in people. But when trust is manipulated, it becomes one of the most powerful attack tools there is. I learned this the hard way long before I ever opened a cybersecurity textbook. When Trust Cost Me My Google Account At the time, I had posted an advert online to promote a product. Not long after, I received a phone call from a man who claimed to be a staff member of the platform where I had placed the advert. He sounded confident, knowledgeable, and helpful. He spoke my language. He explained how I could boost my sales and improve visibility. Naturally, I listened. I wanted my product to succeed. He asked for my email address, and moments later a code was sent to me. He told me the code was needed to activate the boost. Without thinking too deeply, I shared it. Within minutes, I was logged out of my Google account and the platform where I had advertised my product. That was the moment reality hit.Nothing had been “hacked” in the way most people imagine.I had been socially engineered. It took time, persistence, and patience, but I eventually recovered my account. What stayed with me, though, wasn’t just what happened but it was the realisation of how easily trust can be weaponised. And Then It Happened Again, This Time on Facebook Not long after, I experienced something similar with my Facebook page. I was contacted by someone who said I would be writing content for their company and would be paid $20 per post. It felt like recognition. Like opportunity. Like progress. I was excited. They sent me a link. Facebook warned me clearly that clicking “yes” would grant administrative access to my page. I saw the warning. I understood it. And still, I proceeded because in my mind, it made sense. I thought, I will be writing for them anyway. That click cost me my page. Again, there was no system breach.No technical exploit.Just trust, urgency, and optimism used against me. What These Experiences Taught Me Both situations had the same pattern: And the systems did exactly what they were designed to do.The vulnerability wasn not the platform it was the human decision in the moment. This is when cybersecurity stopped being theoretical for me. Why This Changed How I See Cybersecurity These experiences made one thing painfully clear:humans are the first attack surface. Attackers don’t always need advanced tools. They need understanding of behaviour, emotion, fear, ambition, and trust. In both of my experiences, the threat was social engineering.The vulnerability was trust.The risk was underestimated. Why I Didn’t Quit and Why That Matters Losing my Facebook page hurt me but it didn’t end me. I started again.I rebuilt from scratch.Because what was taken was a page not my skills, not my creativity, not my mind. And that resilience matters. Cybersecurity is not about never making mistakes.It is about learning from them and designing systems and behaviours that reduce the chances of repeating them. Trust Isn’t the Enemy Unquestioned Trust Is These experiences didn’t make me paranoid.They made me aware. Cybersecurity doesn’t require us to stop trusting it requires us to verify, slow down, and think critically when emotions are involved. Once I understood this, cybersecurity stopped feeling distant.It became personal. Because at its core, cybersecurity is about protecting humans from attackers, from systems, and sometimes from ourselves. And that is the work I understand deeply.
The Moment I Realised That Cybersecurity Isn’t just Tech: It’s Human Behaviour
I always assumed that cybersecurity was entirely about machines, codes, systems, networks, firewalls. It felt distant, technical, almost like another language spoken on another planet. But along my learning journey, something shifted, I learnt that there is more to Cybersecurity and so many roles come with this field.A truth surfaced quietly, and once I saw it, I couldn’t unsee it: Cybersecurity isn’t just technology.Cybersecurity is people.It’s behaviour. It’s emotion. It’s psychology. There was a single moment where this clicked for me. I was studying social engineering; how attackers manipulate people long before they attack systems and suddenly it felt familiar. I have seen these patterns before. I have lived them. I understood the way humans act under stress, how they hide things, how they panic, how easily trust can be exploited, how fear can make someone hand over information without thinking twice. Aviation had trained me for this without me realising it. In aviation security, we are taught a simple but powerful chain: Threat – anything or anyone that poses danger to civil aviation.Vulnerability – the target exposed to the threat (passengers, aircraft, airline staff, airport).Risk – the likelihood of the threat becoming reality. A formula etched into every cabin crew’s mind: RISK = THREAT + VULNERABILITY And suddenly, it hit me:The weakest link in any system is rarely the system but the human behind it. Once that clicked, everything about cybersecurity changed for me. I started paying attention differently.Not only to the technical steps but to the human steps:the emotional triggers, the motives, the pressures, the subtle manipulation techniques attackers use. It felt familiar, almost like watching an old movie with new subtitles.Aviation had already taught me how to read people, how to sense tension, how to spot inconsistencies, how to evaluate behaviour before words even formed. And that’s when the fear of “starting from scratch” melted a little.Because I realised I was not coming in empty-handed.I was not an outsider.I had been studying human behaviour for years without knowing it was one of cybersecurity’s most valuable skills. In that moment, cybersecurity stopped feeling like a world of machines and started feeling like a world of humans: humans making mistakes, humans being manipulated, humans needing protection, humans creating loopholes without realising it. And I understood something simple but powerful: I am not just learning cybersecurity.I am learning people and I have been doing that all along. Want more like this?I write about human-centred cybersecurity, risk, and career transitions.