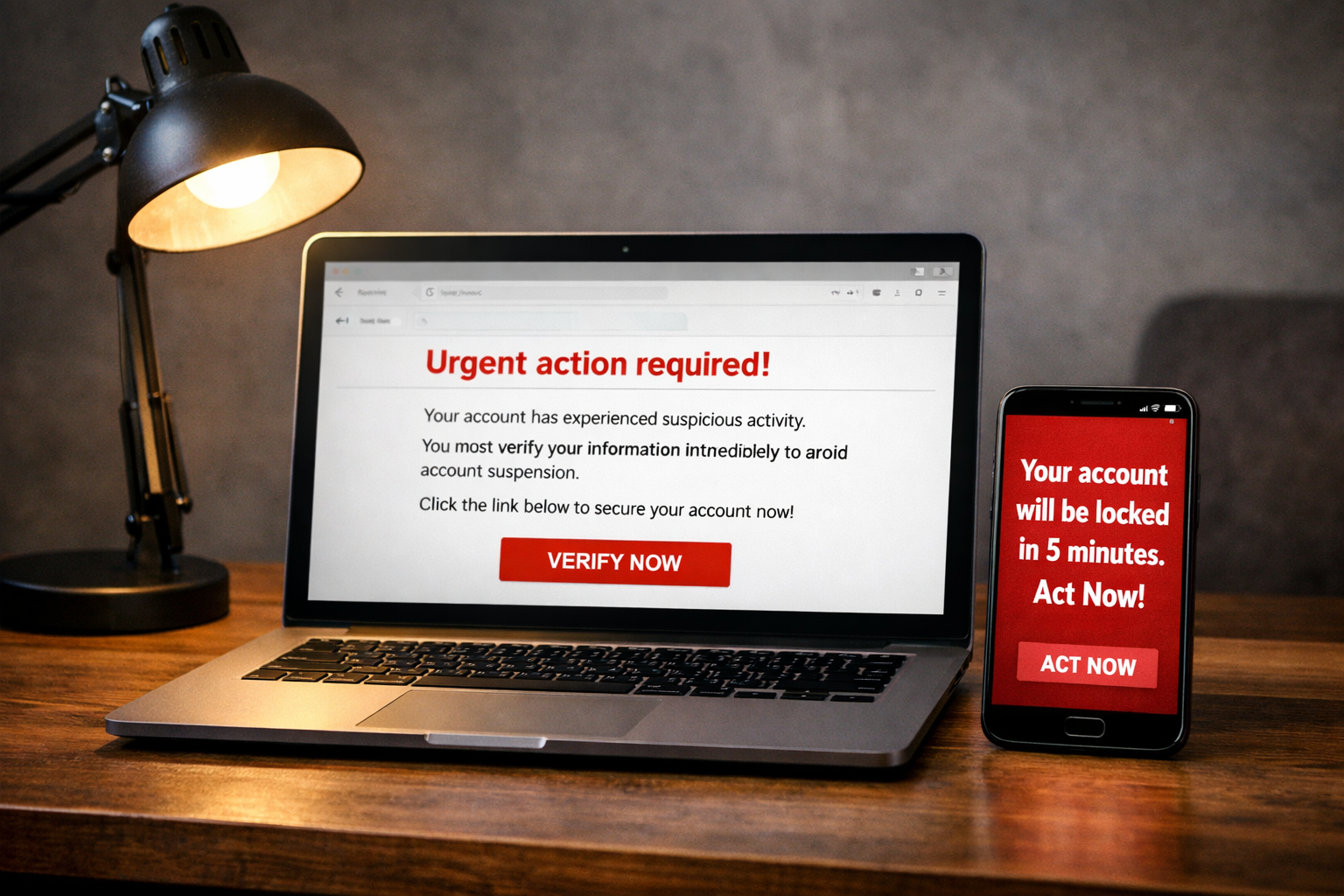
In cybersecurity, many attacks don’t start with hacking tools or technical tricks. They start with one word:
Urgent.
That word has caused more people to lose accounts, money, and data than most viruses or malware. Why? Because the moment something feels urgent, people stop thinking clearly.
Attackers know this very well.
Why Attackers Use the Word “Urgent”
When something feels urgent, fear kicks in. You feel pressure to act fast so you don’t lose something important. Once fear takes over, logic goes quiet.
That’s why attackers use messages like:
- “Your account will be locked in 10 minutes.”
- “Suspicious activity detected. Act now.”
- “Final warning.”
- “Immediate action required.”
The goal is simple:
make you panic so you act without thinking.
Urgency Makes People Skip Checks
When people feel rushed, they don’t verify.
They don’t double-check links.
They don’t ask questions.
They don’t slow down.
They click. They respond. They approve access.
And once that happens, the damage is already done.
Most cyber incidents happen not because someone is careless, but because they felt pressured to act quickly.
Good Security Slows You Down
Strong security systems are designed to slow people down on purpose.
That’s why important actions need:
- confirmation messages
- extra approval steps
- verification codes
- waiting time
These steps are not there to annoy you.
They are there to protect you when emotions are high.
Urgent Does Not Always Mean Real
Not everything urgent is true.
Real companies give you time to verify.
Real problems can be checked through official channels.
Fake urgency falls apart when you pause and question it.
The Real Skill Is Control
Cybersecurity is not about acting fast.
It is about acting wisely.
When you slow down, you take back control.
And when you take back control, most attacks fail.
Final Thought
If a message tells you to act immediately, pause.
Take a breath.
Verify first…..
Never Trust, always verify!
Want more like this?
I write about human-centred cybersecurity, risk, and career transitions.